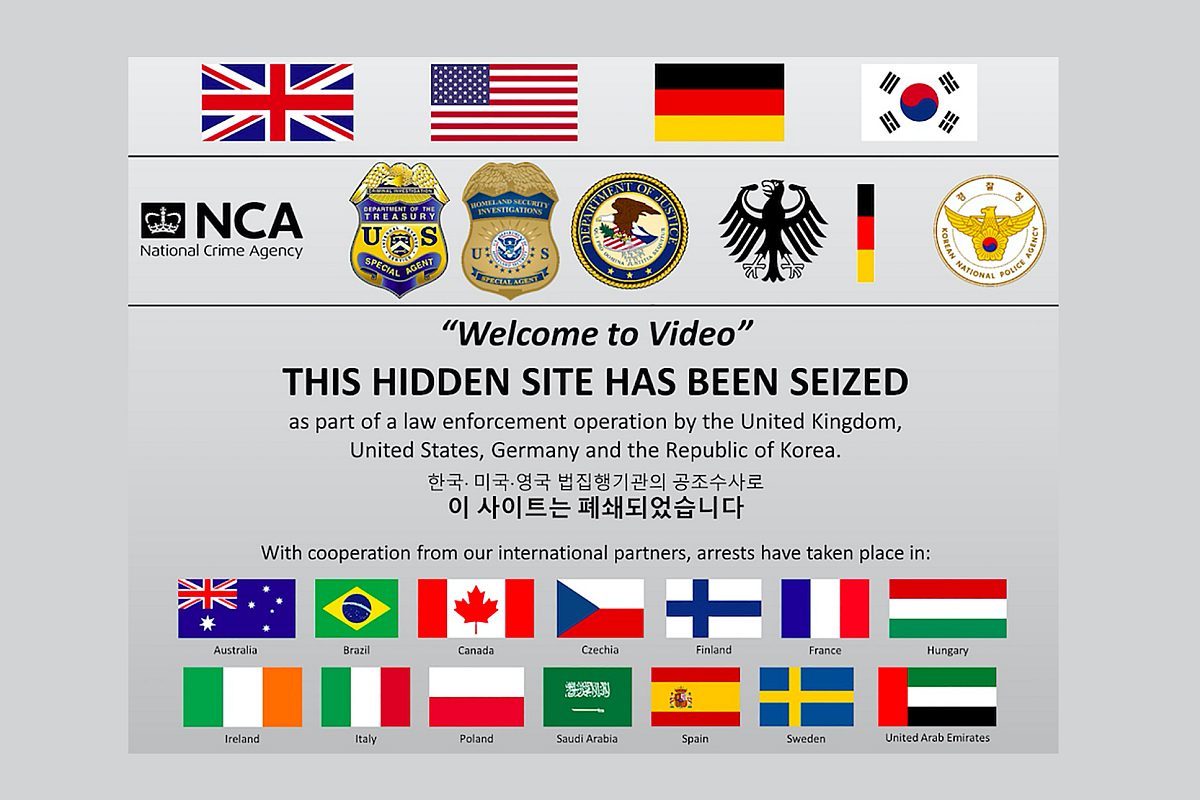
American, British and South Korean officials announced at a news briefing on Wednesday that they have busted the massive dark web child-porn site ‘Welcome to Video’. The site generated and distributed exploitative content, and had an infrastructure in place that could have supported up to a million users.
An analysis of a server, seized by South Korean authorities, revealed that the website had more than one million bitcoin addresses, signifying that the website had a capacity for at least one million users, Dawn newspaper reported. According to the report, the operation led to the rescue of at least 23 minor victims residing in the United States, Spain and the United Kingdom, who were being actively abused by the users of the site.
Advertisement
The internet-based child pornographic network was the world’s largest child sexual exploitation market by volume of content, said US Deputy Assistant Attorney General Richard Downing. The site’s operator, 23-year-old Jong Woo Son of South Korea, has already been charged and convicted by South Korean officials and is currently serving his sentence there.
Officials said hundreds of suspects had been charged worldwide for their alleged involvement with the largest darknet child pornography website, funded by Bitcoin. The takedown is notable also for the investigation that enabled it, which focused not on offensive hacking efforts or surveilling encrypted communications but on tracing bitcoin transactions.
The nine-count indictment was unsealed on Wednesday along with a parallel civil forfeiture action. Son has also been charged and convicted in South Korea and is currently in custody, serving his sentence in South Korea.
Authorities have also arrested 337 other users in the US states of Alabama, Arkansas, California, Connecticut, Florida, Georgia, Kansas, Louisiana, Maryland, Massachusetts, Nebraska, New Jersey, New York, North Carolina, Ohio, Oregon, Pennsylvania, Rhode Island, South Carolina, Texas, Utah, Virginia, Washington State and Washington, DC.
According to the Dawn report, some of the suspects were arrested in the United Kingdom, South Korea, Germany, Saudi Arabia, the United Arab Emirates, the Czech Republic, Canada, Ireland, Spain, Brazil and Australia.
“Darknet sites that profit from the sexual exploitation of children are among the most vile and reprehensible forms of criminal behaviour,” said US Assistant Attorney General Brian A. Benczkowski. “This administration will not allow child predators to use lawless online spaces as a shield.”
He said the US Department of Justice was working closely with partners in South Korea and around the world to rescue child victims and bring to justice the perpetrators of the abhorrent crimes. Chief of the US Internal Revenue Service’s Criminal Enforcement Don Fort told the news briefing that their agents played a key role in busting the network.
According to the indictment, agents from the IRS, HSI, National Crime Agency in the United Kingdom, and Korean National Police in South Korea arrested Son and seized the server that he used to operate a darknet market that exclusively advertised child sexual exploitation videos available for download by members of the site.
Officials seized 8 terabytes of child porn videos during the investigation and site takedown, which included more than 250,000 unique videos. Law enforcement officials and the National Center for Missing and Exploited Children are analyzing the footage to potentially identify more children and perpetrators of exploitation. Almost half of the videos seem to be previously unknown to officials.
Welcome to Video made money by charging fees in bitcoin, and gave each user a unique bitcoin wallet address when they created an account. Son operated the site as a Tor hidden service, a dark web site with a special address that helps mask the identity of the site’s host and its location. But Son and others made mistakes that allowed law enforcement to track them. For example, according to the indictment, very basic assessments of the Welcome to Video website revealed two unconcealed IP addresses managed by a South Korean internet service provider and assigned to an account that provided service to Son’s home address. When agents searched Son’s residence, they found the server running Welcome to Video.
To “follow the money,” as officials put it in Wednesday’s press conference, law enforcement agents sent fairly small amounts of bitcoin; roughly equivalent at the time to $125 to $290 to the bitcoin wallets Welcome to Video listed for payments. Since the bitcoin blockchain leaves all transactions visible and verifiable, they could observe the currency in these wallets being transferred to another wallet. Law enforcement learned from a bitcoin exchange that the second wallet was registered to Son with his personal phone number and one of his personal email addresses.
The investigation extended beyond Son as well. Law enforcement agents worked with the blockchain analysis firm Chainalysis to map user transactions with Welcome to Video wallets and attempt to trace individuals who interacted with the site. Chainalysis says that during the three years it operated, Welcome to Video received almost $353,000 worth of bitcoin from thousands of transactions. By charting the web of Welcome to Video users’ assigned wallets and the bitcoin wallets or exchanges they used, officials identified several US-based cryptocurrency exchanges that users had gone through to pay for their Welcome to Video viewing.
(With input from agencies)